Let’s Encrypt SSL certificate and IIS
Overview
In todays world it should be obvious that no website should be run without securing it with a certificate. Unfortunately, I have seen cases where this is still true, and the ‘reasons’ are combination of:
It’s not available from the public.
It’s only a dev environment.
I don’t want to go through the hassle with the IT.
I used Let's Encrypt service to get SSL certificates for my private web server.
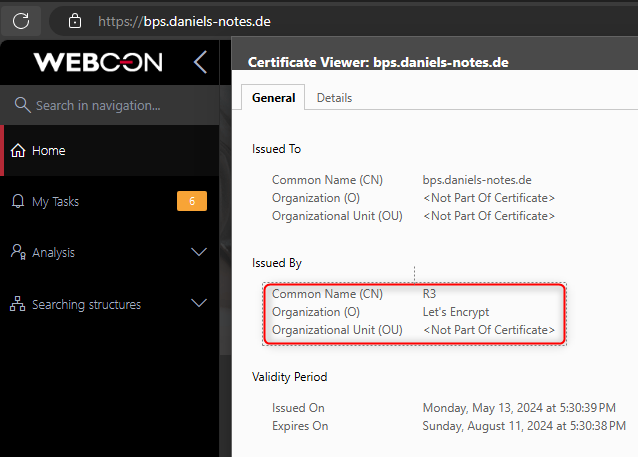
I’m not sure whether I have documented all initial steps to get it up and running. So, I will just provide a few information and links to the original site and go into more detail to use it with IIS.
Remark: I don’t have qualified experience in this area. There may be better ways out there, but this is how I got it working and I’m providing the information as is.
Get a SSL certificate
I’ve been using certbot to get a certificate for my site. Since I’m using IIS, I selected Web Hosting Product on Windows
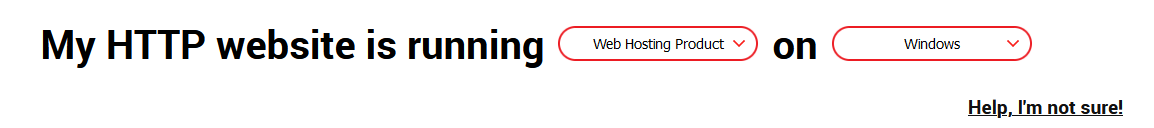
The page provides detailed instructions. If my notes are valid then I’ve used the following command line to get an SSL certificate for bps.daniels-notes.de.
#certbot doesn't work from PowerShell ISE
certbot certonly --standalone -d "bps.daniels-notes.de"
I’m using the --standalone parameter because no other site is using port 80.
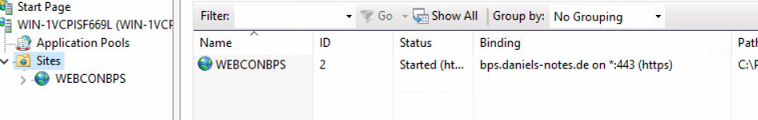
With the command a folder for the site was created and the necessary files have been downloaded.
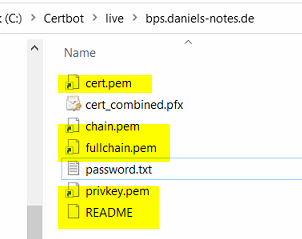
Creating the .pfx file for IIS
After the files have been downloaded, I was provided with the next hurdle. How can I take these files so that I can use them with IIS. The way I found was to use OpenSSL for windows to create a .pfx file from those files.
- Extracted the package to the folder
C:\Install\SSLCertificate\OpenSSL-1.1.1h_win32 - Create a password.txt in the certbot folder with the password to use. In my case the folder is:
C:\Certbot\live\bps.daniels-notes.de.
The below script will switch to the site folder, use the string password to generate the .pfx file.
cd C:\Certbot\live\bps.daniels-notes.de
#C:\Install\SSLCertificate\OpenSSL-1.1.1h_win32\openssl pkcs12 --help
$password = Get-Content "password.txt" -Encoding UTF8
C:\Install\SSLCertificate\OpenSSL-1.1.1h_win32\openssl pkcs12 -export -in cert.pem -inkey privkey.pem -out cert_combined.pfx -password pass:$password
Adding the certificate for the site
Now that we have the certificate, the rest is easy.
- Import the certificate.
- Add it to the site in IIS
You can do it manually or use the below script. It will store the certificate in the personal certificates folder.
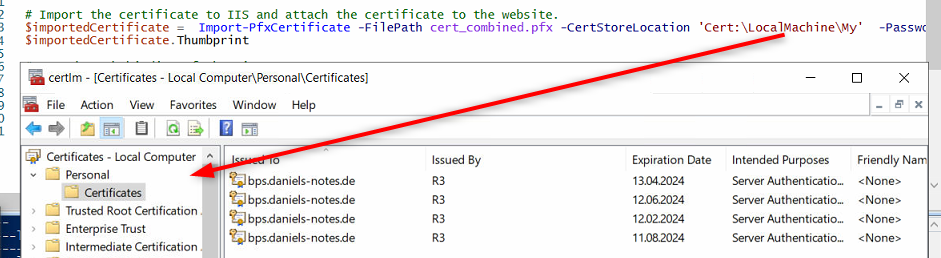
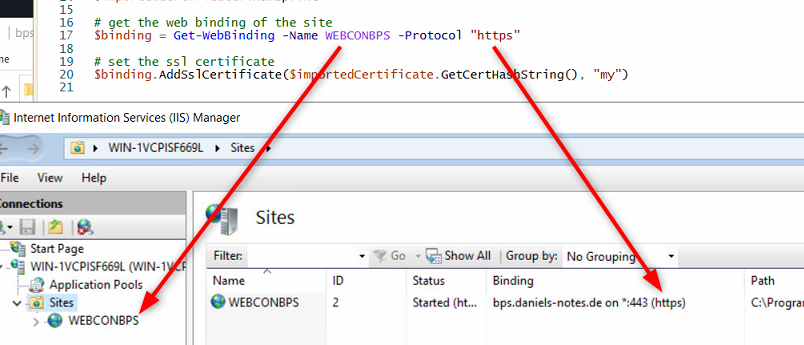
The certificate will then be added to the site with the name WEBCONBPS. This site should have a single https binding.
cd C:\Certbot\live\bps.daniels-notes.de
# Import the certificate to IIS and attach the certificate to the website.
$importedCertificate = Import-PfxCertificate -FilePath cert_combined.pfx -CertStoreLocation 'Cert:\LocalMachine\My' -Password (ConvertTo-SecureString -AsPlainText $password -Force)
$importedCertificate.Thumbprint
# get the web binding of the site
$binding = Get-WebBinding -Name WEBCONBPS -Protocol "https"
# set the ssl certificate
$binding.AddSslCertificate($importedCertificate.GetCertHashString(), "my")
Updating the certificate
Each certificate will expire after 90 days. Since no one want’s to update the certificate manually, the easiest way would be to add a task to the windows task scheduler to do everything.
Luckily the installation of certbot already created Certbot Renew Task for us, which checks twice a day, whether certificate files need to be updated.
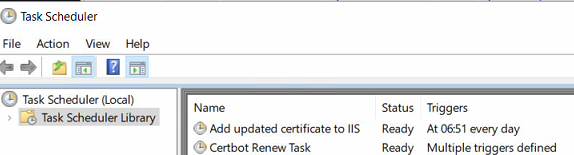
All that’s left is to add a task for the other steps. I’ve put all the code into an install.ps1 file.
#certbot certonly --standalone
#certbot --help
#certbot doesn't work from ISE
#certbot certonly --standalone -d "bps.daniels-notes.de"
# Generate the .pfx file
cd C:\Certbot\live\bps.daniels-notes.de
#C:\Install\SSLCertificate\OpenSSL-1.1.1h_win32\openssl pkcs12 --help
$password = Get-Content "password.txt" -Encoding UTF8
C:\Install\SSLCertificate\OpenSSL-1.1.1h_win32\openssl pkcs12 -export -in cert.pem -inkey privkey.pem -out cert_combined.pfx -password pass:$password
# Import the certificate to IIS and attach the certificate to the website.
$importedCertificate = Import-PfxCertificate -FilePath cert_combined.pfx -CertStoreLocation 'Cert:\LocalMachine\My' -Password (ConvertTo-SecureString -AsPlainText $password -Force)
$importedCertificate.Thumbprint
# get the web binding of the site
$binding = Get-WebBinding -Name WEBCONBPS -Protocol "https"
# set the ssl certificate
$binding.AddSslCertificate($importedCertificate.GetCertHashString(), "my")
Afterwards I’ve added a task:
- Choose a name and schedule to your liking
- Add an action to run a program and execute PowerShell to execute the script file
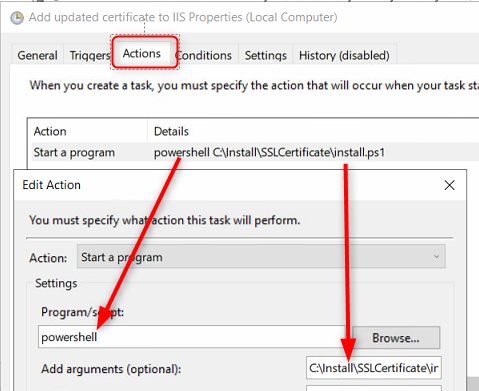
Run the script from an action. - Ensure that you ticked
Run whether user is logged on or not. It may be necessary to also tickRun with highest privilegesbut this is something you need to check on your system.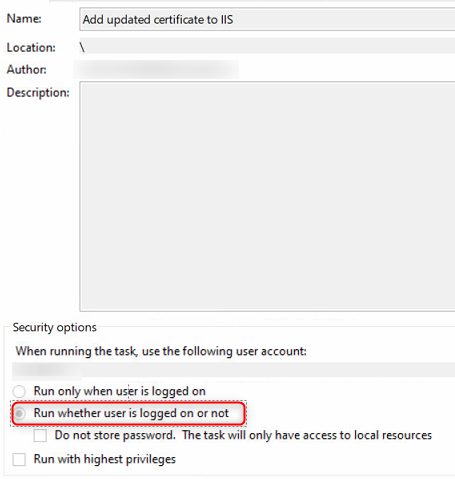
The task should be executed regardless whether the user is logged in or not.
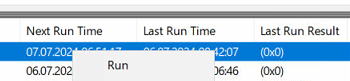
Run the script from the context menu to verify, that it works. The Last Run Result should be 0x0.
Comments